Storing Azure App Service secrets on Azure Key Vault

Today I'm going to show how to store Azure App Service configuration secrets on Azure Key Vault. In this example, I'm going to use a DNN Platform based website deployed on Azure App Service using a SQL Database, storing the SQL database connection string in Azure Key Vault. I won't change the application codebase to access the Azure Key Vault in any way. We Will take advantage of the App Service managed identity feature to automatically retrieve the Key Vault secrets.
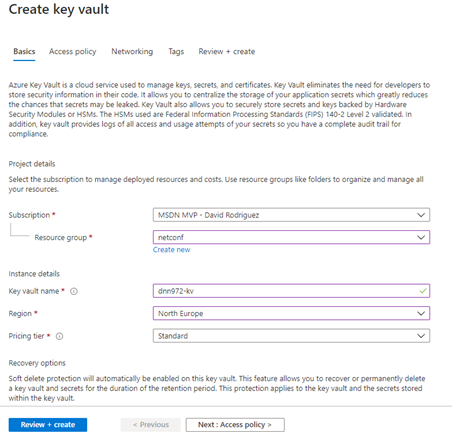
Provision the Azure Key Vault
-
Provision the Azure Key Vault
-
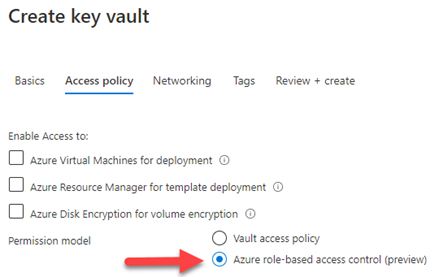
For this demo, we will change the permissions model to the new Azure role-based access control (RBAC). It's currently in Preview.
-
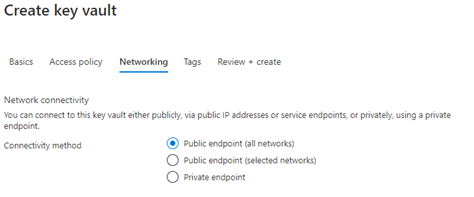
Depending on your deployment, change the Networking as desired. For this demo we will leave it as Public endpoint to match the App Service configuration
- Click on the Review + Create button to start the deployment
-
Once created, add yourself to the role "Key Vault Administrator (Preview)" via the Access Control (IAM). Now you can start managing secrets.
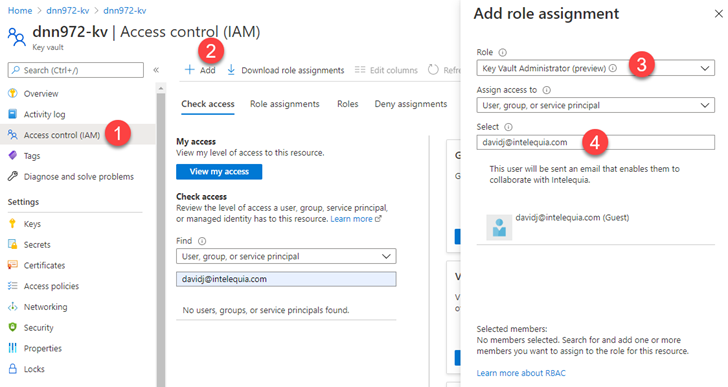
Add the Connection String to the Key Vault secrets
-
Add a new secret to the Key Vault
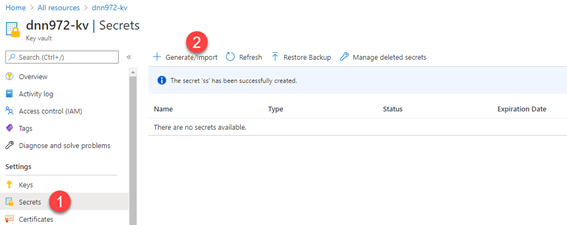
-
Specify the secret of type "Manual", give it a name and set the value to the current SQL Database connection string stored in the Application web.config
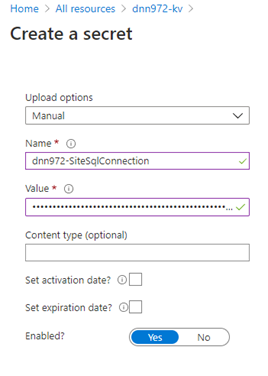
- Click on Create. Once created, click on the secret to see the secret details, and then click again on the current version
-
Next to the Secret Identifier, click on the copy to the clipboard button
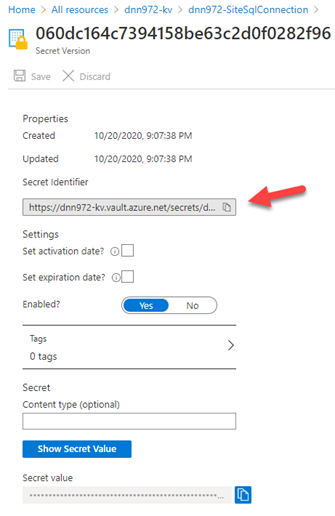

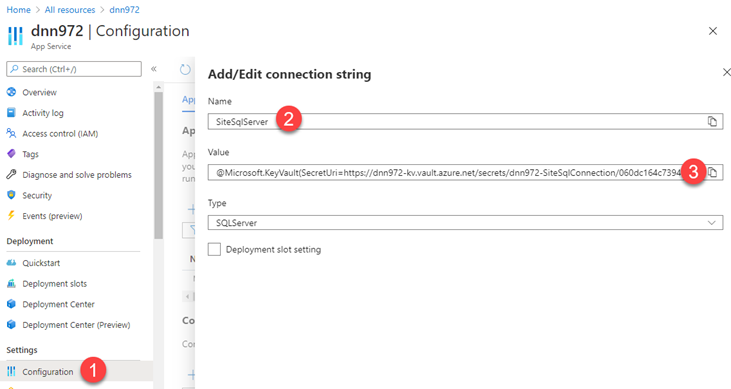
Add the secret identifier reference to the Azure App Service Settings
- Open the App Service configuration settings, and add a new Connection String setting
- Type the name of the connection string ("SiteSqlServer" for DNN Platform) and set the value "@Microsoft.KeyVault(SecretUri=VALUE_FROM_CLIPBOARD)", where the VALUE_FROM_CLIPBOARD is the one from step 4 in previous section.
-
Click on Save to save the app settings
Allow the App Service to access the Key Vault
- On the App Service again, click on Identity to enable the System Assigned identity.
-
Click on save after turning "On" the status
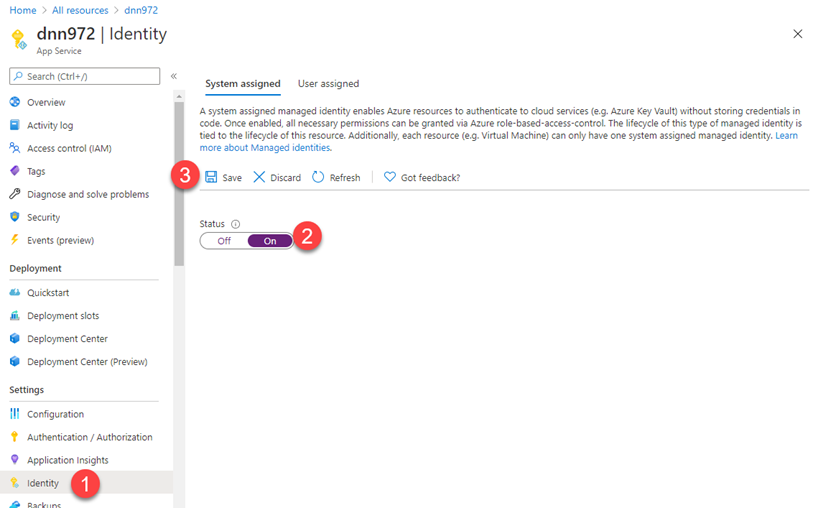
-
Click on the "Role Assignments" button and then click on the "Add role assigment (Preview)"
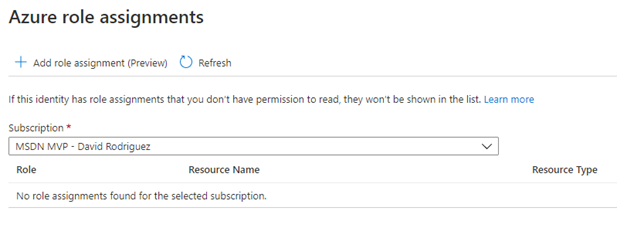
-
In the role assignment, choose scope "Key Vault", subscription the subscription where you created the Key Vault on previous steps and the name of the Key Vault resource. For the role just select "Key Vault Secrets User (preview)"

-
Finally go to the web.config file of your DNN Platform website and clear the connection string contents.

- Visit the website and check that loads successfully. Now the connection string is safely stored in the Azure Key Vault, and it's no longer stored on the file system.
Known issues
-
ERROR: You get an error "Keyword not supported: '@microsoft.keyvault(secreturi'". I have experienced that the RBAC permissions can take a one or two minutes to be applied, so try after a few minutes. Also try restarting the application thought the App Service portal so nothing is cached.

- When checking the DNN log4net logs, you see lot of errors from a process trying to initialize a database connection with an invalid connection string during the DNN initialization process. This error is currently happening on versions 9.7.2 or earlier with a pending pull request to fix it https://github.com/dnnsoftware/Dnn.Platform/issues/4227
- IMPORTANT: If you plan to use the Azure App Service Backup feature, don't use this method to store SQL Database connection strings in Azure Key Vault, since the App Service backup feature doesn't support them https://stackoverflow.com/questions/56101504/backingup-azure-webapp-when-connection-string-is-injected-through-keyvault
Hope this helps!