Why is Microsoft a leader in security?

Every day we are receiving news of different trying to breach cybersecurity attacks in companies, both large and small. We always say that as long as it does not happen in our organization, everything is fine, or at least we think so. Every time I meet, in meetings on cybersecurity issues, with different customers and hear endless arguments from IT managers on the one hand and by the management of the company either CEO or Finance Department on many occasions things go through my mind that I can not tell.
In my daily work you can find the heads of IT departments completely overwhelmed by the amount of work due to the decisions of CEO and responsible financial departments in which economic value takes precedence over effective and efficient technological solutions for their companies, implementing a myriad of technologies, unconnected to each other, which must manage the IT departments overwhelmed.
This decision making based exclusively on the financial part and not on the technical part makes these companies run very high risks.
Thinking that this IT attack will never happen to me, has made many companies take unnecessary risks and make them inoperative for weeks or months, and even close the company because of the impossibility of continuity due to the loss of all the data.
On the other hand, it is also necessary to take into account the business reputation, since on the one hand, it takes into account those attacks due to the lack of technical resources made available to the IT department versus attacks impossible to stop in spite of those resources implemented, which in the latter case, can exonerate, to a great extent, the company of responsibilities with its clients and with the competent administrations.
Microsoft's security tools allow a unified, agile and easily executable management, which allows an organization to have the highest standards of security and regulatory compliance are those provided by Microsoft within a wide range of security solutions that are at the top of the different quadrants of Gartner 2022.
Did you know that Microsoft is the largest security company you've never heard of, and the breadth and strength of its security platform is proof of that?
Despite being recognized for enterprise productivity and desktop solutions, Microsoft invests billions of dollars every year in security research and development, integrating those advances into the products and services it relies on every day.
That continued investment means Microsoft Security continues to be named a leader in four Magic Quadrants by Gartner. This achievement recognizes vendors that demonstrate continuous effort in execution and vision, with a strong focus on technology development and meeting the needs of their customers now and in the future.
The four security areas in which Microsoft has been named a leader are as follows:
- Access Management
- Enterprise Information Archiving
- Unified Endpoint Management (UEM) Tools
- Endpoint protection platforms
Microsoft delivers best-of-breed and best-of-breed suite
Microsoft's strength in these areas is not isolated either, one of Microsoft's top priorities has been to ensure that their solutions integrate seamlessly to provide greater cohesion and visibility.
Because of the scale of the technology they build and operate, Microsoft can capture a diversity of threat signals from sensors to customers to back end cloud services and share that data with their customers.
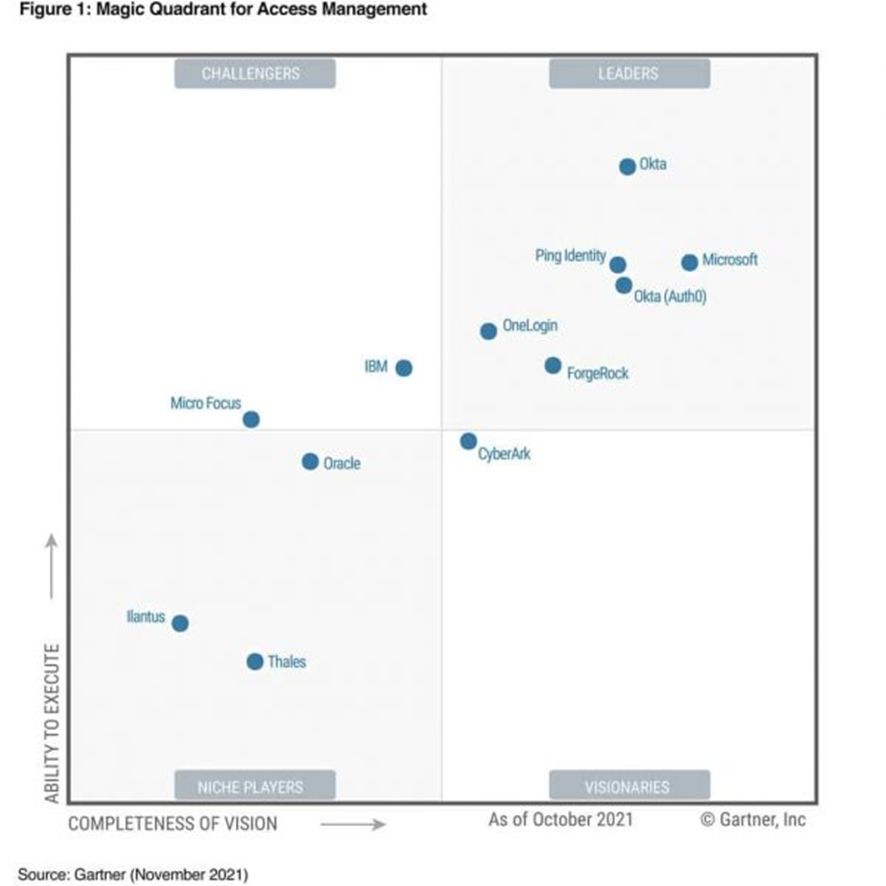
A leader in access management
Its Azure AD product is sold in bundles and focuses on delivering access management as part of a converged SaaS IAM (Identity and Access Management) platform for internal and external access management use cases. Its operations are geographically diversified and its customers vary in size and industry. A large portion of Microsoft's customers use its products for workforce scenarios.
Recent product innovations include the addition of FIDO2 support (for passwordless authentication), an agent for access management for and adaptive access for CIAM. In fact, Microsoft plans to invest 10% of its security revenue in R&D for risk protection in Multicloud infrastructures to improve and enhance the capabilities of identity and credentialing functions in a decentralized manner.
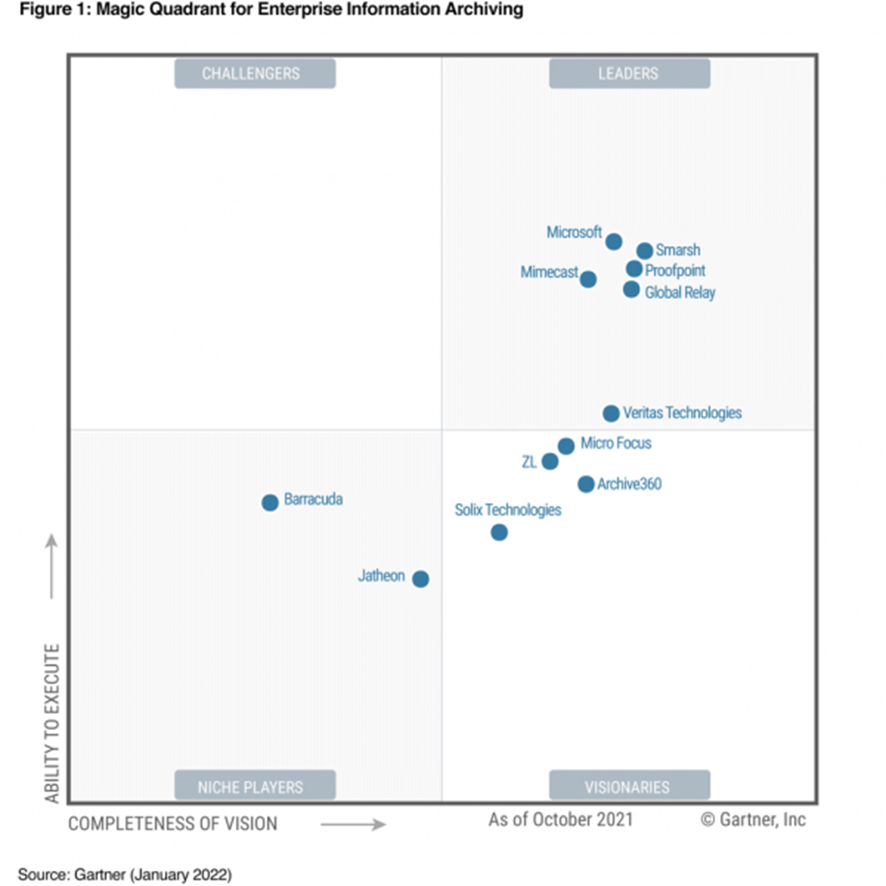
Leader in enterprise information archiving
Microsoft's archiving solution is based on the Microsoft 365 SaaS platform introduced in October 2015 . Microsoft's EIA (Enterprise Information Archiving) solution is designed for a variety of application/user generated data sources and digital communication, operating worldwide and intended for SMBs and large enterprises.
In addition, over the past 12 months, Microsoft has included support coverage to enable the integration of multiple sources outside of Microsoft 365 Compliance Manager customer-centric assessments; and the ability to collect and review encrypted content from SharePoint and OneDrive, including records management, compliance, and end-user archiving.
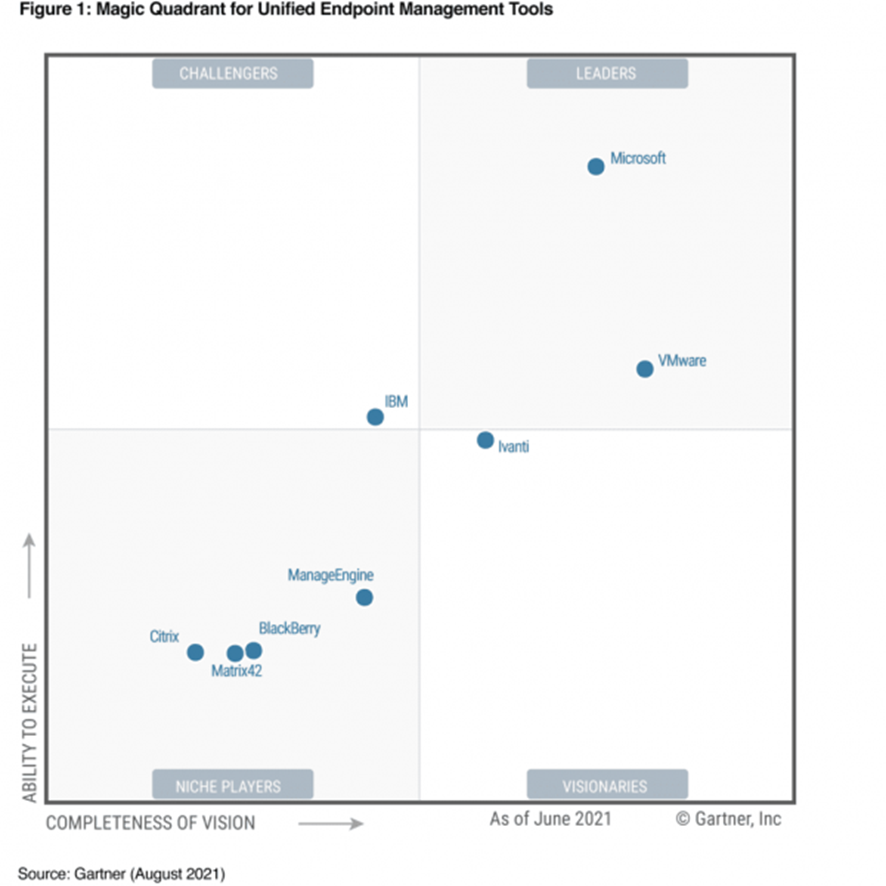
Aimed at serving offshore customers and improving the IT administrator experience, analytics and automation of Endpoints that support frontline workers' devices, the Microsoft Endpoint Manager solution combines Intune and Configuration Manager and is available with an Enterprise Mobility + Security (EMS) license capable of integrating with Azure Virtual Desktop, Windows 365, Defender for Endpoint and AAD (Azure Active Directory)
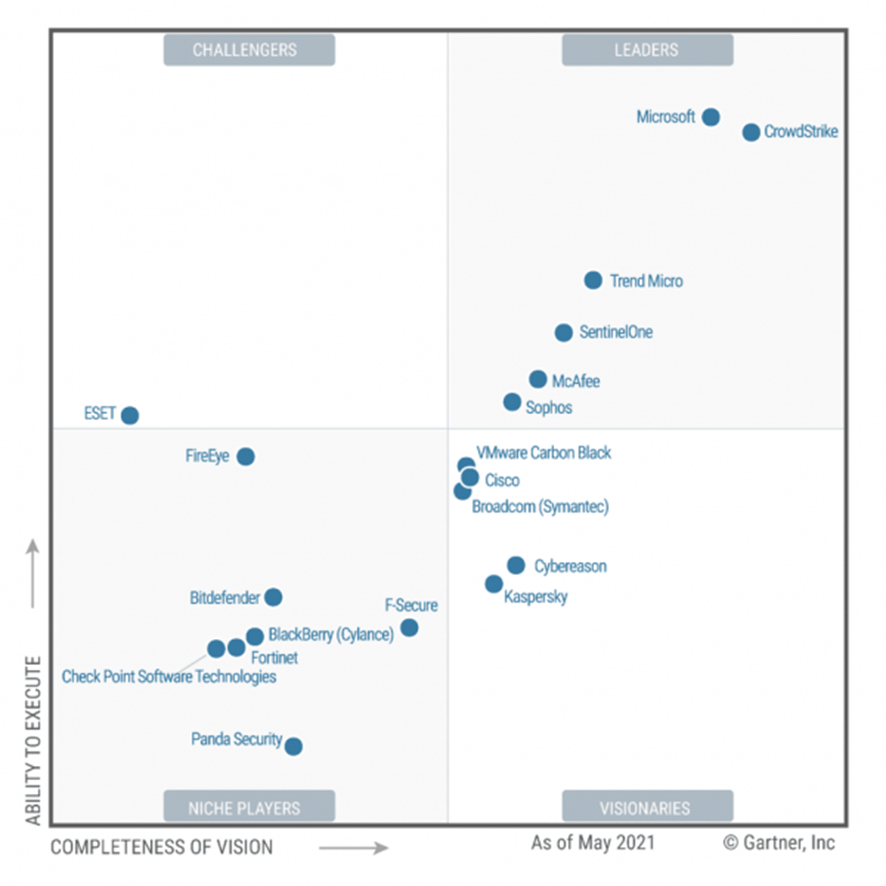
The leader in endpoint protection platformsMicrosoft Defender for Endpoint (MDE) provides an integrated and comprehensive set of EPP, EDR, including threat scanning capabilities from a single cloud-hosted console and data lake. The native protection and prevention provided by Defender Antivirus on the Windows operating system has broad coverage that allows it to be leveraged by other vendors as we see in this magic quadrant.
In addition, Microsoft invested in its operating system coverage in 2020, introducing significant new macOS and Linux protection capabilities, coverage for Android and iOS devices and even introduced improvements in threat and vulnerability management
Microsoft's solutions appeal to all types of organizations globally, and its solutions can be deployed regardless of business size and tailored to the specific needs of each organization.
Ready to secure your digital transformation journey with Microsoft Security?
No matter where you are in your transformation journey, our team of experts is ready and willing to help you make the most of Microsoft Security solutions.
Intelequia is one of the few specialized companies with a dedicated Microsoft Security practice. Our expertise in this space is reflected in our Microsoft Partner of the Year Security Awards 2022 finalist status. Our consultants work exclusively with Microsoft security solutions to provide a variety of managed and professional services.
Find out how you can leverage the best of Microsoft security solutions combined with our expertise to protect your environment. If you have any inquiry, please feel free to contact us. We will be glad to help you😊
llegar a hacer cerrar la empresa por imposibilidad de continuidad debido a la pérdida de todos los datos.