Having a good cybersecurity strategy in place in any organization is more important than ever. One of the biggest challenges facing businesses today is DDoS (Distributed Denial of Service) attacks. In this article, we will explore what they are, how to identify them and how to protect your business from them.
What is a DDoS Attack?
A DDoS attack occurs when multiple systems compromise and send an overwhelming amount of traffic to a server, website or network, with the goal of overloading system resources and making them inaccessible to legitimate users. These attacks can be devastating, causing significant disruptions and, in some cases, financial losses.
How to Identify a DDoS Attacks
Being able to identify a DDoS attack quickly is crucial to minimizing damage. Speed in identifying and responding to a DDoS attack is critical to minimize the negative impact on a number of fronts: technical, financial, operational and reputational. Taking proactive measures and having an effective response plan are essential components of a robust cybersecurity strategy. Here are some signs that your company could be the victim of a DDoS attack:
1. Extreme Network Slowness: One of the first signs is a noticeable slowdown in network speed. This slowness not only affects the user experience, but can also jeopardize daily operations, causing service interruptions and overloading infrastructure resources.
2. Unusual Traffic Surge: A sudden and unexpected spike in web traffic can be a sign of an attack. Identifying this unusual increase quickly is important to activate mitigation measures as soon as possible, thus avoiding further damage and economic losses.
3. Service Interruptions: Users may experience difficulties accessing websites or online services. These interruptions can erode customer confidence and damage the company's reputation, especially if they are prolonged over time due to late identification.
4. Connection Errors: An increase in HTTP errors, such as 503 (Service Unavailable), is a clear indication. These errors not only affect the user experience, but can also be costly in terms of downtime and recovery.
5. Anomalous Network Behavior: Monitoring your network for unusual traffic patterns can help identify ongoing DDoS attacks. The ability to detect and respond to these anomalous patterns quickly is vital to maintain the integrity and availability of services, as well as to comply with regulations and avoid penalties.
Early detection of a DDoS attack not only helps minimize damage and maintain service availability, but also reduces financial losses, preserves a company's reputation, and ensures regulatory compliance.
How to Protect Your Business from DDoS Attacks
Protecting your business from a DDoS attack requires a combination of preventive and reactive measures. Here are some key steps with specific Microsoft Azure technologies:
1. Use a CDN (Content Delivery Network)
CDNs (Azure Content Delivery Network) help distribute traffic efficiently and can mitigate the impact of an attack by absorbing malicious traffic before it reaches your server. Azure CDN offers fast and secure delivery of content to users via globally distributed servers, helping to disperse network traffic.
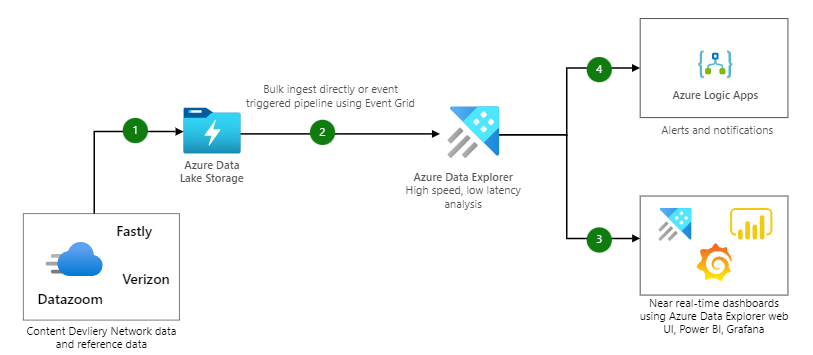
Content Delivery Network
2. Implement a Web Application Firewall (WAF)
A WAF (Azure Web Application Firewall) can filter and monitor HTTP traffic to your server, blocking attacks targeting specific layers of the application. Azure WAF protects web applications from common vulnerabilities and attacks, such as SQL injection and XSS (Cross-Site Scripting) attacks.
3. Use Anti-DDoS Services
Azure offers specialized services to mitigate DDoS attacks. Azure DDoS Protection detects and neutralizes malicious traffic before it reaches your network, with advanced mitigation and real-time analysis capabilities designed specifically for Azure applications.
4. Real-Time Monitoring and Alerting
Implementing real-time monitoring systems will allow you to detect unusual spikes in traffic and activate security protocols quickly. Azure Monitor provides a comprehensive, real-time analysis of the performance and operability of your infrastructure. Azure Security Center adds to these capabilities with advanced security features and personalized recommendations.
5. Have an Incident Response Plan
Having a detailed plan for responding to a DDoS attack can be the difference between a minor incident and a devastating outage. Azure Automation allows the creation of runbooks to automate incident responses. Azure Sentinel, a SIEM (Security Information and Event Management) solution, facilitates orchestration and automated threat response, ensuring rapid intervention.
6. Staff Training
Ongoing training of your IT team is vital. Make sure they know how to identify DDoS attacks and how to activate the necessary security protocols. Microsoft Learn offers educational resources and training on cloud security. Microsoft Defender for Identity offers advanced protection and visibility into insider threats, helping to train your team on security best practices.
Protecting your business from DDoS attacks is crucial in today's digital environment. Identifying the signs of an attack and taking protective measures, such as using a CDN and web application firewall, can help you mitigate risks. In addition, a real-time monitoring system and a robust incident response plan are essential to ensure business continuity.
At Intelequia, we are committed to cybersecurity and protecting your digital assets. If you would like to learn more about how we can help you strengthen your security, don't hesitate to contact us.