Protect your documentation with Azure Information Protection

IT security has become a recurring and priority subject in all organizations around the world in recent years as a result of teleworking. Ensuring the protection of systems and information has often not become a simple task, raising many recurring questions such as: Who has access to my data?
Who has access to my data? How can I find out if they were shared with people outside the organization? or What security measures can I apply? Is it possible to restrict access to certain users?
It is here where just a few years ago Microsoft developed a new service to help us protect corporate information: Azure Information Protection, but what is really useful?
What is Azure Information Protection and what is it for?
Azure Information Protection or AIP is a Microsoft cloud-based service that protects corporate email, documents and confidential data through an encryption system.
Through the application of tags to the content, AIP maintains absolute control over all information and can delimit actions for authorized users and maintain centralized control over all company documentation, regardless of whether it is stored anywhere either in a local environment or in the cloud.
A service designed to ensure the security of documentation and legal compliance of information.
Advantages of working with AIP
1) Classify data according to the degree of confidentiality: The IT Team or administrators will be able to configure policies that classify, label and protect data according to the degree of confidentiality automatically or based on recommendations.
2) Ongoing protection: By allowing information to be classified, data is always protected regardless of whether it is stored locally or in the cloud or by whom it is shared.
3) Data monitoring and analysis: All corporate documentation can be monitored and reports can be prepared to analyze the actions of the organization's users.
4) Guarantee internal and external collaboration in a secure environment: Maintaining control over access to information internally will allow you to define which roles are allowed to share information outside the organization and work within it in a much safer way.
5) Integrations with other solutions: Azure Information Protection allows you to integrate its document classification and control capabilities with Microsoft 365 and other common applications with a single click, allowing you to facilitate universal protection within the organization.
6) Choice of encryption keys: Whether they are on-premises or in the cloud, including Bring Your Own Key (BYOK) and Hold your On Key (HYOK) options.
In which practical cases can AIP help you?
- Legal Compliance: For example with GDPR or other regulations.
- 360º Tracking: Identifying at all times who, how, when and what documents have been opened by team members.
- Sensitive Documentation Control: Allowing to revoke access to former team members or people outside the organization.
- Internal Protection: For example, if someone were to take a pen drive with company information and insert it into another PC outside the organization, they would not be able to access the information.
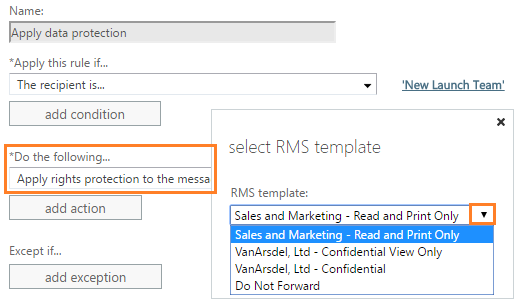
- Restricted e-mails: Being able to guarantee the delivery of e-mails to only authorized recipients.
And what is ARM or Azure Rights Management?
We can not talk about AIP without identifying what is the Azure Rights Management technology also known by its acronym ARM, basically it is the system that allows to protect confidential information of an organization against unauthorized access through security policies and data encryption for emails or attachments.
In this way, any member of the organization could share sensitive information with external users via email through a secure environment ensuring that only certain users can open a document, in addition to preventing printing or forwarding.
Do you want to know more?
Request more information